Portal Customization
You can customize the appearance of your portal by navigating to the Customize section.
The Customization feature allows you to tailor the login page of your Enterprise Portal to align with your organization's branding. This feature enables you to modify key elements to create a consistent and professional appearance that reflects your corporate identity.
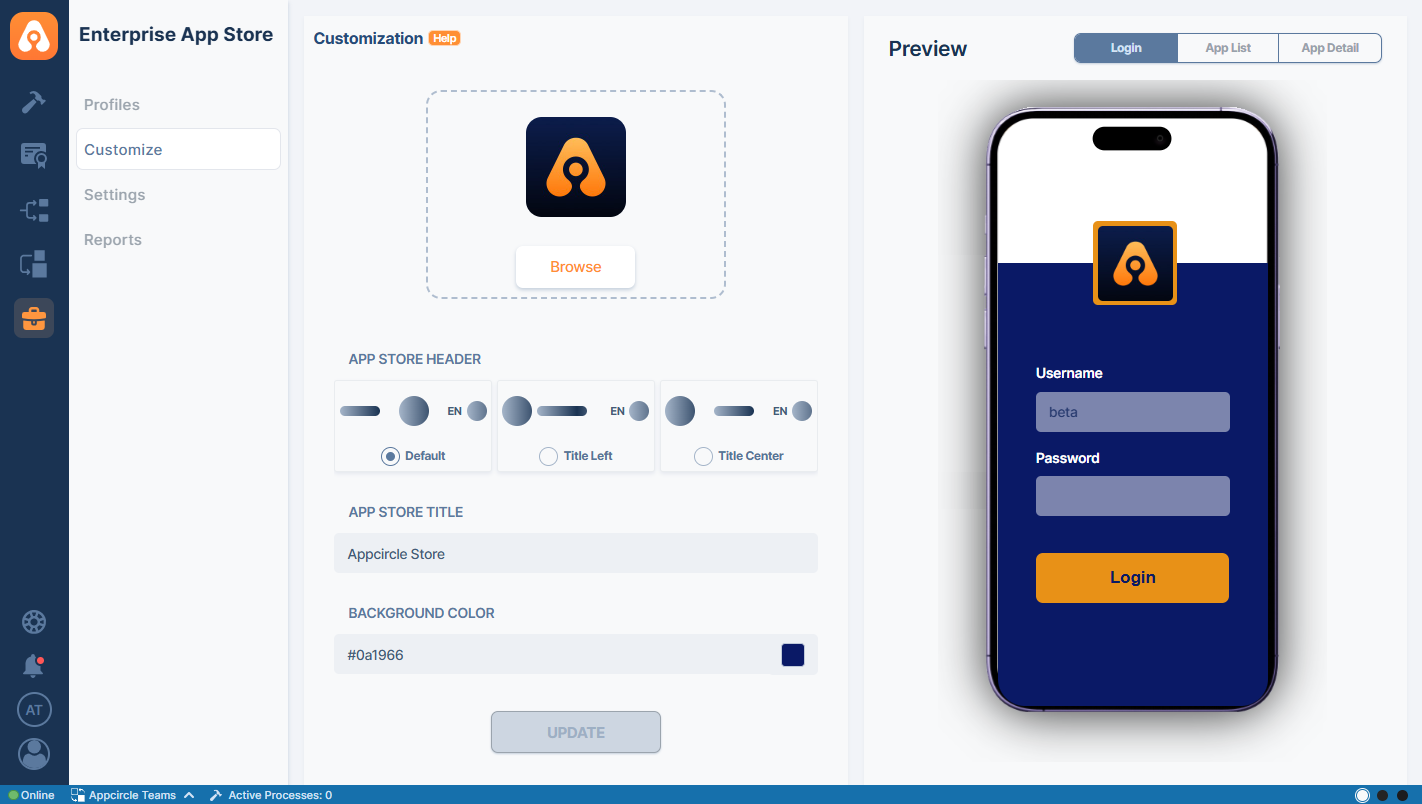
- Logo: Replace the default logo with your company’s logo to reinforce brand recognition.
- App Store Header: Choose from three options to customize the positions of your store title and logo on your App Store header: Default, Title Left, or Title Center.
- App Store Title: Personalize the title displayed on the login page. You can update it to include your company name or any other relevant text that suits your brand.
- Colors: Customize the color scheme of your login page, including the background, text, and button, to reflect your brand’s unique palette.
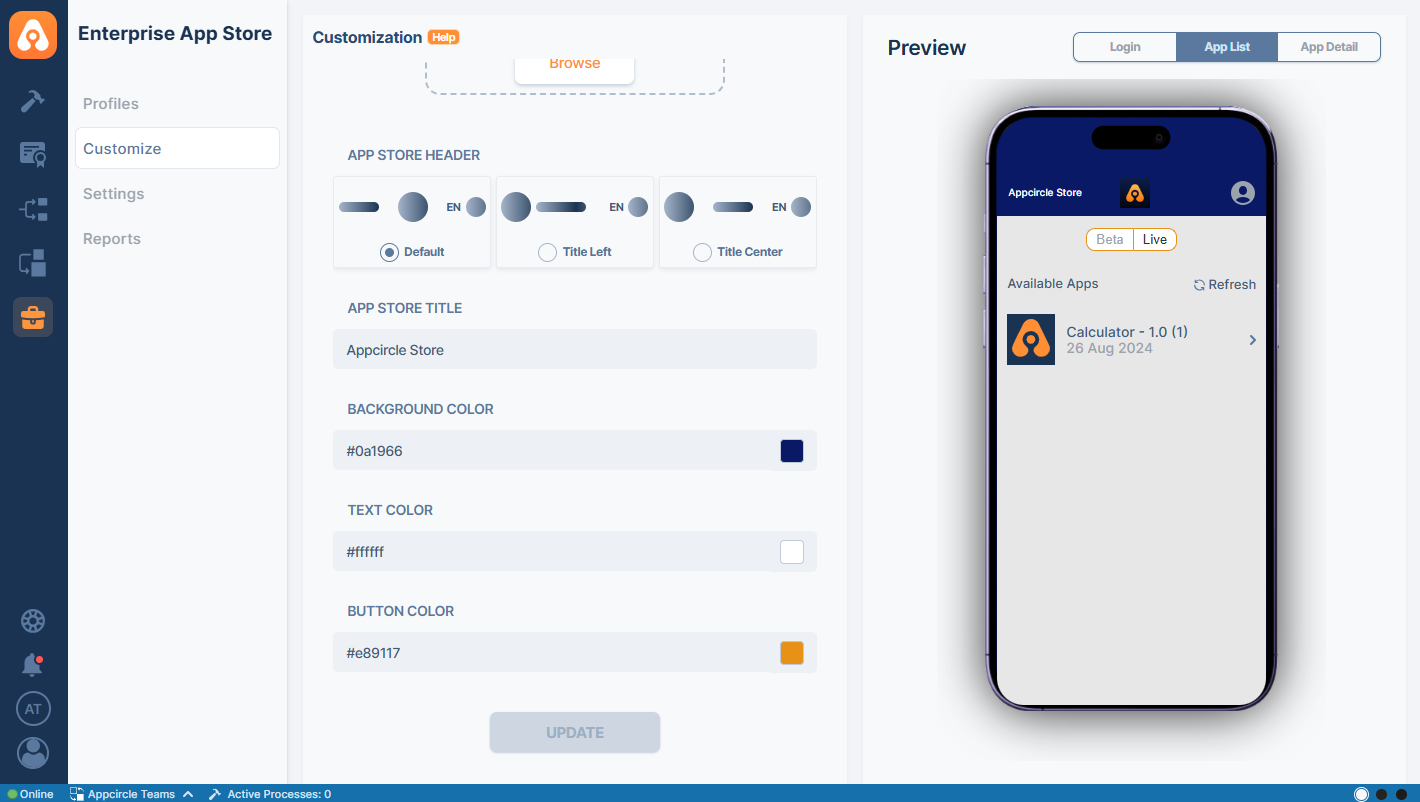
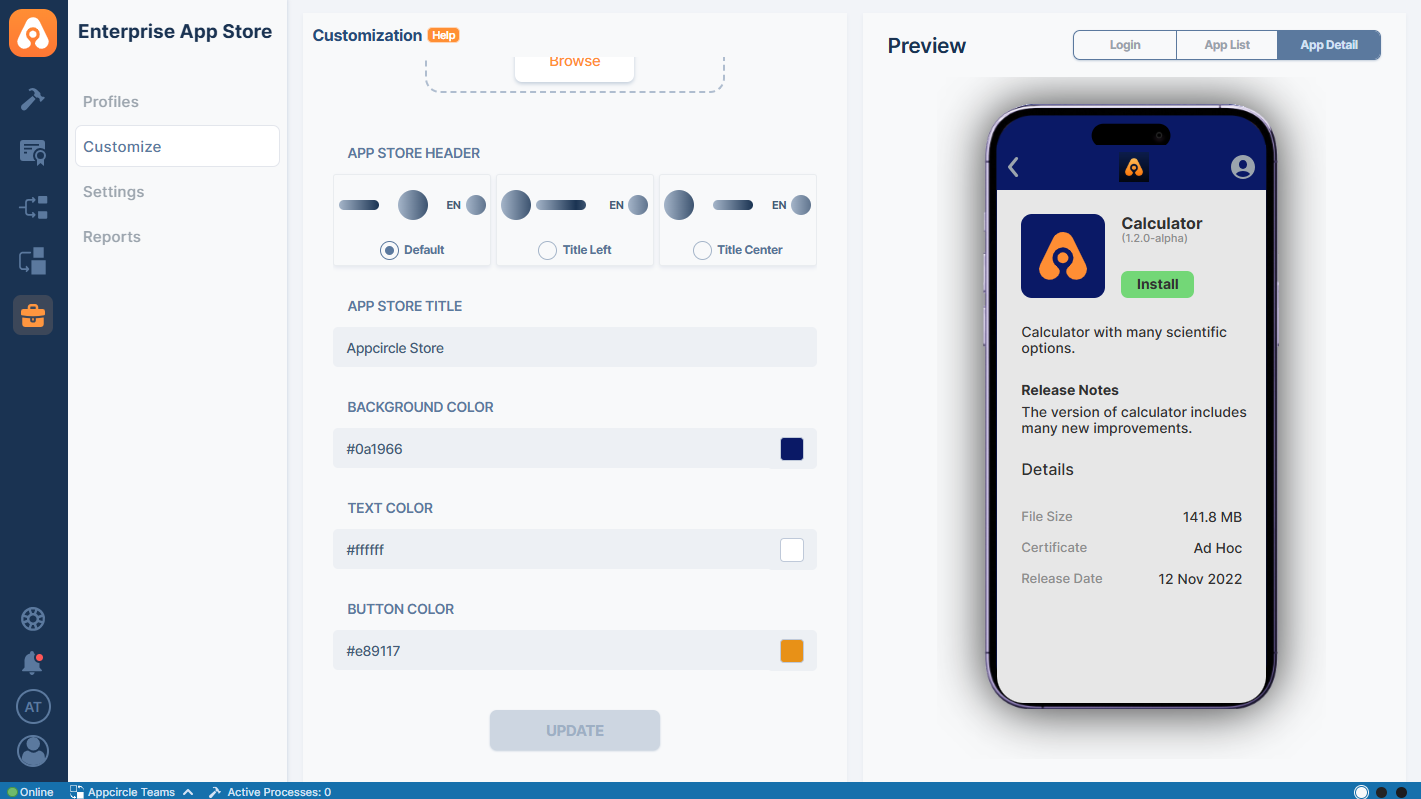
The preview screen allows you to view changes in real time before saving them. The preview screen displays the Login screen, App Details screen, and App List screen as you customize your Enterprise Portal.
- Login
- App List
- App Detail

If you are working on a sub organization, you will not have access to Customize and Settings sections on Enterprise App Store module. Only the root organization has the privilege to Set up, Configure and Customize the Enterprise Portal.